THE CHALLENGE IS HOW DO I ELIMINATE BLIND SPOTS IN INDUSTRIAL ENVIRONMENTS?
In network terminology, "blind spots" refer to segments of a network that obscure or impede data analysis, potentially compromising both the performance and security of the network.
These blind spots can arise from various factors, including but not limited to:
Unplanned Network Expansion
- New equipment or applications have been added without adequate planning or architectural adjustment, leading to areas where data becomes "hidden."
- Teams responsible for overseeing the data need to be correctly organised or briefed, leaving gaps in network surveillance and management.
Complex Deployment Strategies
- Adding new deployments can make the network more complex, which may lead to the creation of blind spots.
- New equipment can be used to incorporate new links or remote locations, but it can be challenging to maintain a seamless overview of data processing and network activities.
SPAN Port Challenges
- SPAN ports, while essential, can foster blind spots through contention issues, packet dropping, and incorrect programming.
- These issues can lead to losing vital information, resulting in incorrect or incomplete data captures that can seriously hinder network performance and security.
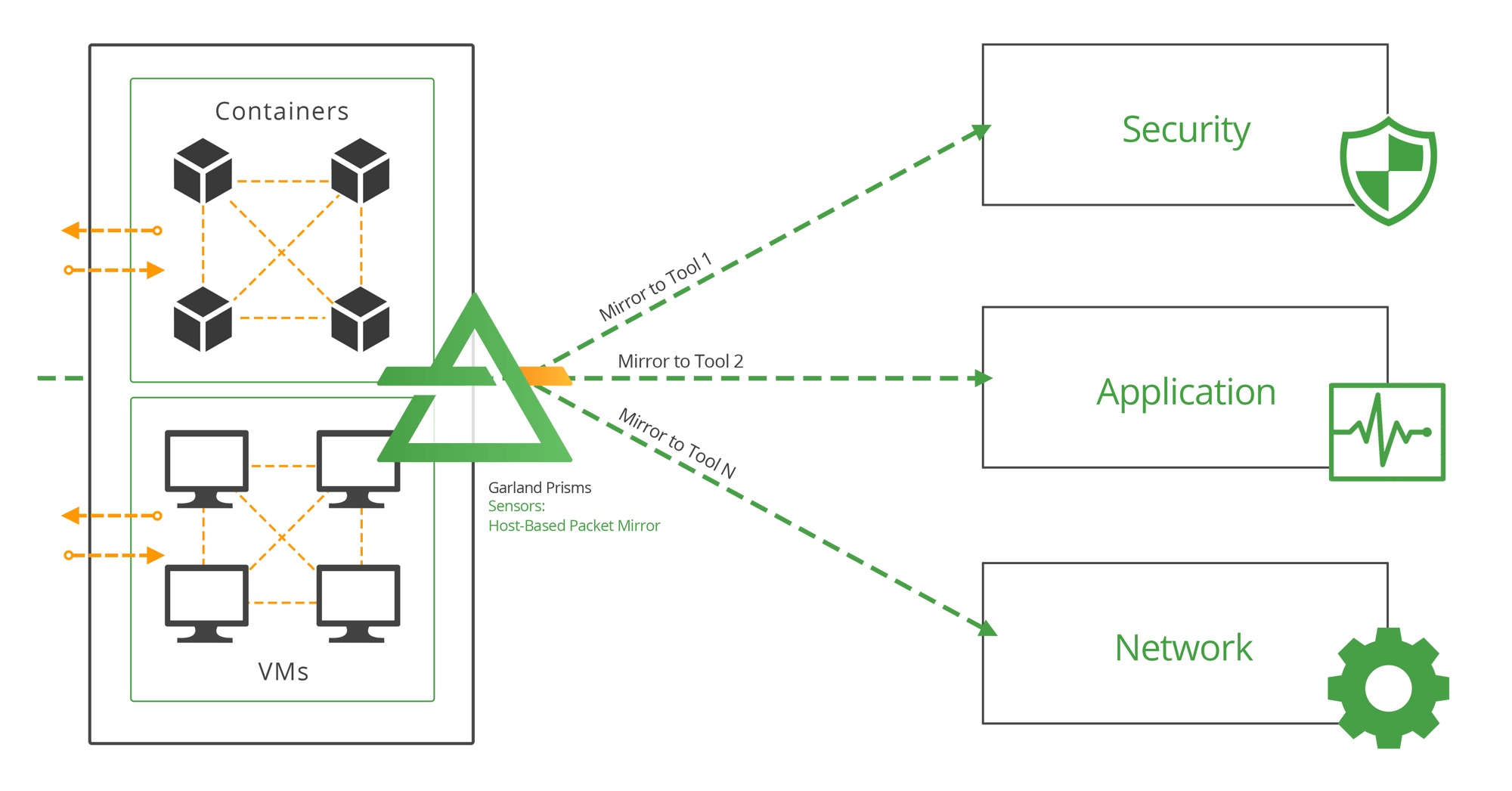
Virtualisation-Induced Blind Spots
- Adopting a virtualised data centre environment can create new areas where potential problems may go undetected.
- Blind spots are more prevalent with the increased use of technologies such as Kubernetes and containers.
- However, the industry is making advances in implementing better mirroring technology to tackle this issue.
A Well-lit Path to Network Stability
It is essential to understand the underlying causes of network blind spots to avoid potential pitfalls. To create a highly secure, efficient, and responsive network, you must proactively identify and address these issues.
Don't let blind spots keep you in the dark. Take charge and explore comprehensive strategies and cutting-edge solutions to illuminate every corner of your network.
THE SOLUTION
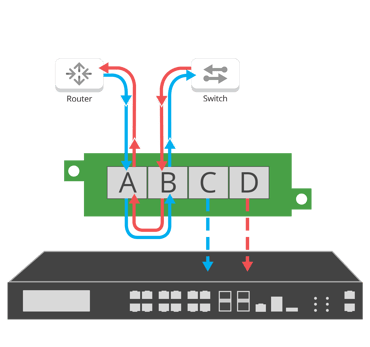
Network TAPs guarantee tools complete packet data.
Network performance monitors (NPMs) can be used to determine areas within a network that aren't performing as they should, letting you know where the problem is located. Network TAPs, an industry best practice over SPAN ports, create a "foundation of visibility," providing the ability to capture network monitoring data without compromising the network, removing blind spots.
"Research found that 83 percent of current network visibility fabrics use TAPs for at least half of the fabric access layer." -EMA [Enterprise Management Associates]
Network TAPs are used to help IT teams easily monitor all network data. A network TAP is a purpose-built hardware device that allows you to access and monitor your network traffic by copying packets without impacting or compromising network integrity.
They are typically placed between any network devices like switches, routers, and firewalls, creating an exact copy of both sides of the traffic flow continuously, 24/7/365. The duplicate copies can be used for monitoring, security, and analysis while the network flow continues uninterrupted. TAPs do not introduce delay or alter the data. They are either passive or "failsafe," meaning traffic continues to flow between network devices if power is lost or a monitoring tool is removed.